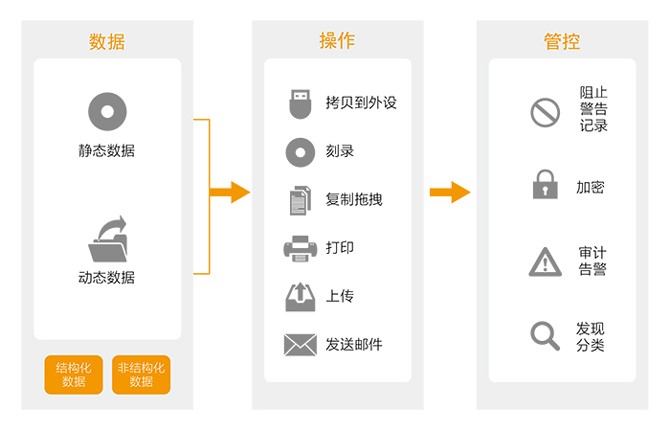
Sensitive data leakage protection system is content recognition technology based on data security protection of design drawings, source code, the text of the contract, financial statements and other sensitive documents, to prevent disclosure of data via email, chat tools, SkyDrive, U disk copy and print the way for users to leak recording, alarm, blocking, and audit on user behavior. Effectively identify sensitive data, monitor sensitive data usage, and protect sensitive data leakage. Effectively train and improve employees' awareness of sensitive documents.
Core function:
1.full data life cycle protection
You can parse files such as Word, Excel, PPT, Pdf, Txt, compressed format, identify sensitive data, and locate sensitive data easily in the form of document embedding. To achieve proactive defense, the overall control of things, the goal of the post event audit, to achieve sensitive data can be protected, security situation can be measured, security events can be traced.
2. Meet compliance requirements
To control and control sensitive documents of enterprises, and protect the risk of data leakage.
3.all-round intelligent protection
U disk copy, QQ, hair, printing, cloud disk and other ways to prevent leakage channels to prevent and control, to protect customer data security.
Product characteristics:
1, the content of recognition can be used to identify the contents of the terminal through the file type, keywords, regular expressions, such as fingerprint data method, and analyze Chinese segmentation based on semantics, effective identification of sensitive documents.
2, data protection: you can mail, client, shared files, QQ, Tencent and other real-time communication software effective protection, to avoid through file sharing, mail attachments, QQ chat and other ways to disclose sensitive information.
3, port control: USB, Bluetooth, printers and other peripherals port control, prohibit the adoption of U disk copy, print and other ways to carry out sensitive information leakage.
4, audit analysis: classified audit, comparative analysis of the leak. And carries on the statistical analysis to the tendency.
Deployment plan: